Anxun Leak Notes
I-SOON leak was one of the most prevalent leaks in the past. Security researchers were able to extract new insights from the Chinese-nexus APT groups.

Anxun Leak Analysis
In this post, I want to share my findings from the recent infamous Anxun Leak.
Overview and Brief
- Initial Source of Leak – GitHub Repository
- Company Website – i-soon.net
- Company Name – Shanghai Anxun Information Technology Co.
- Company Information – PitchBook Profile
- Data Analysis and Highlights – GitHub Repository
Shanghai Anxun Information Technology Co. provides IT security consulting services, including risk assessments, firewall/penetration testing, APT attack protection, and program audits, enabling enterprises to conduct IT operations more securely. The company operates similarly to NTC Vulcan, functioning as a significant cyber-offensive contractor for tool development and cyber operations.
The leak possibly originates from an insider aiming to expose the company's activities, although it could also serve as a cover for another operation. The leaked data consists of key elements highlighted by the whistleblower:
- Anxun's relationships with National Security Agencies in China
- Employee data
- Financial documents
- Chat records between Anxun members
- Internal documentation of Anxun products
- Evidence of Anxun’s infiltration into foreign entities, including NATO countries, South Korea, and the US
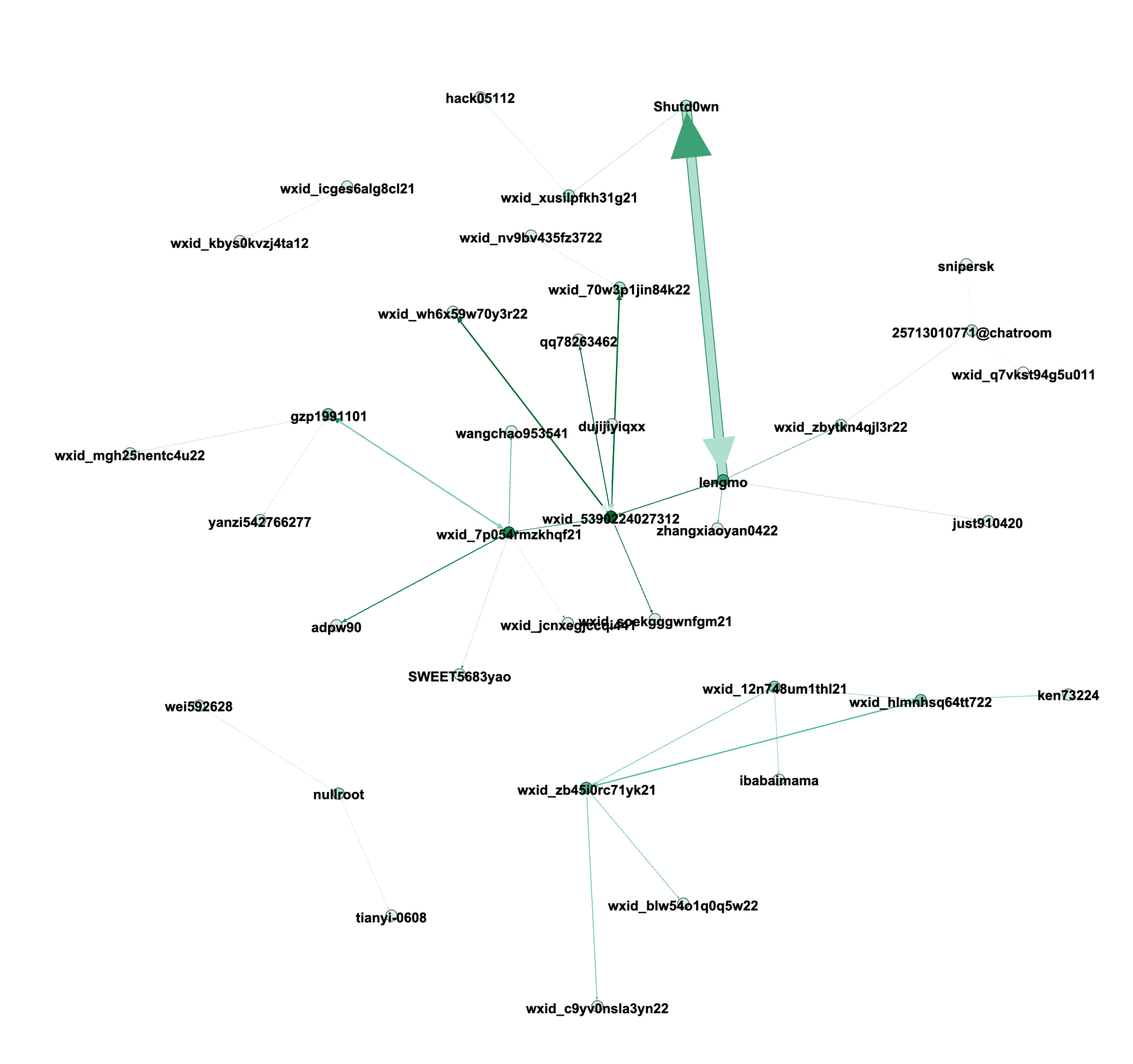
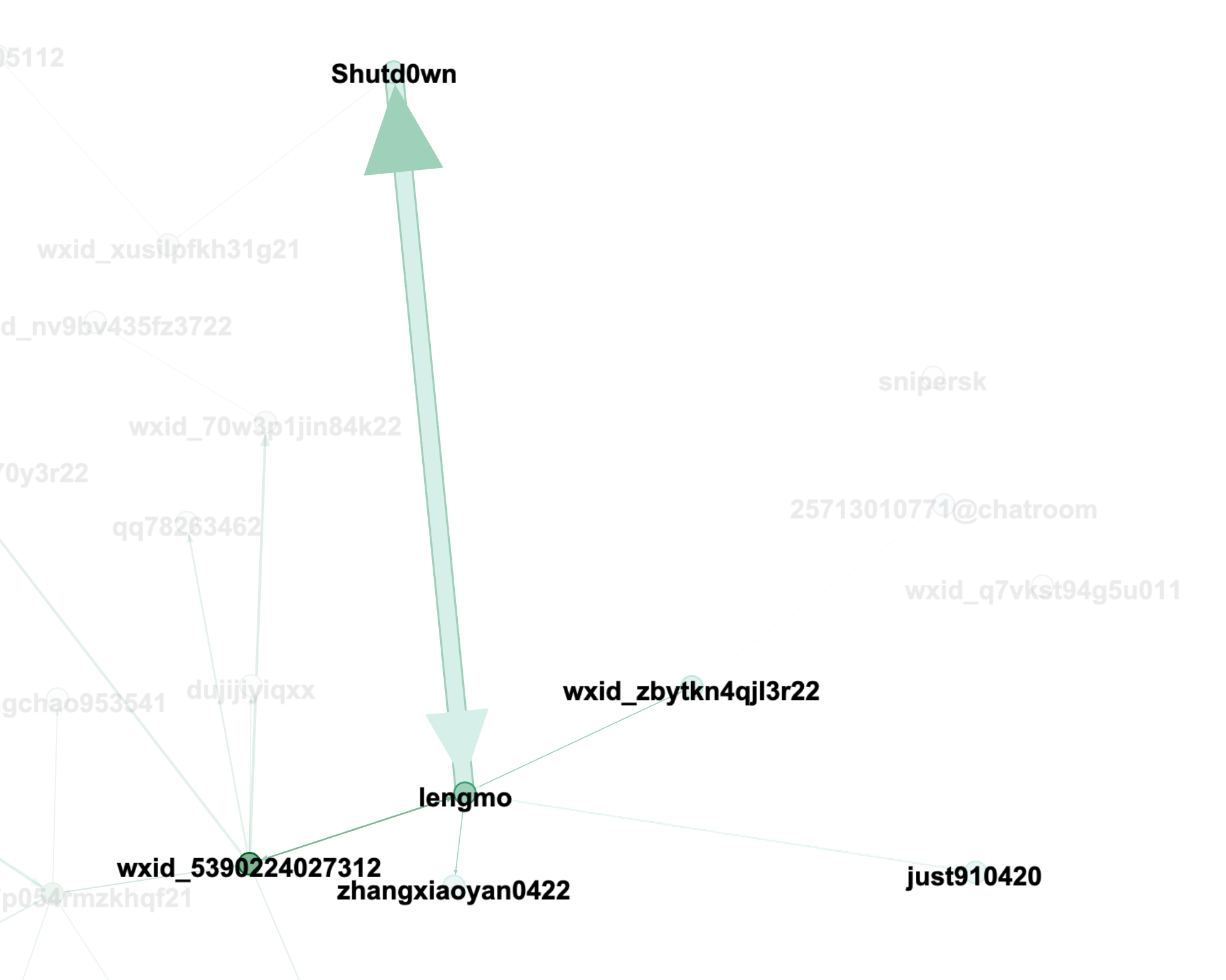
Chat Overview
The chat logs primarily come from a WeChat chatroom (where wxid_* is a unique ID assigned to users by the WeChat system).
Top Message Senders
| Sender | Count Messages |
|---|---|
| lengmo | 4981 |
| Shutd0wn | 3675 |
| wxid_5390224027312 | 1409 |
| wxid_7p054rmzkhqf21 | 894 |
| wxid_wh6x59w70y3r22 | 620 |
Top Message Receivers
| Receiver | Count Messages |
|---|---|
| Shutd0wn | 4661 |
| lengmo | 3987 |
| wxid_5390224027312 | 1611 |
| wxid_7p054rmzkhqf21 | 804 |
| wxid_zb45i0rc71yk21 | 697 |
Chat Graphs