Obsidian Impersonation Phishing Campaign
Threat actors allegedly have started using combination of GoogleAds and SEO Poisoning to trick users, reroute them to the phishing websites and download fake version of Obsidian

Summary
Threat actors allegedly have started using a combination of Google Ads and SEO Poisoning to trick users, reroute them to phishing websites, and download a trojanized version of Obsidian.
It has been recently reported on the Obsidian subreddit about one such fake website that threat actors have started abusing.
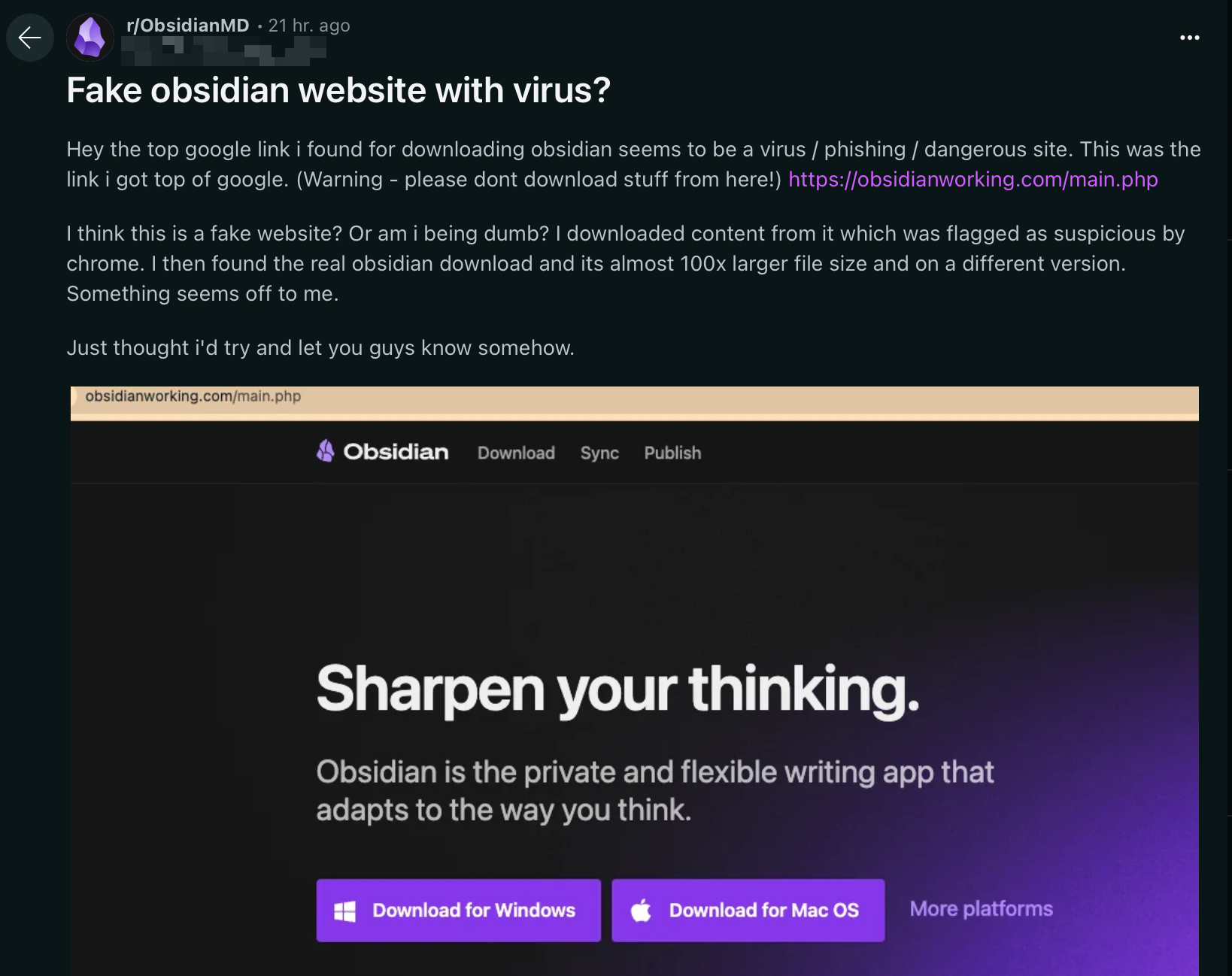
What is Obsidian?
Obsidian is a personal knowledge base and note-taking software application that operates on Markdown files. It allows users to create internal links for notes and visualize the connections as a graph. It is designed to help users organize and structure their thoughts and knowledge in a flexible, non-linear way. (Wikipedia)
Basically, it is a very powerful note-taking application with sync capabilities, plugins, and publishing features (btw, I’m using Obsidian to create this note).
Why Obsidian to Trick Users?
Obsidian is gaining popularity as an advanced version of the already popular note-taking application CherryTree. Especially after the recent survey published by StackOverflow, which highlighted the rising popularity of Obsidian. Threat actors follow trends, which is why Obsidian has become a good phishing target.
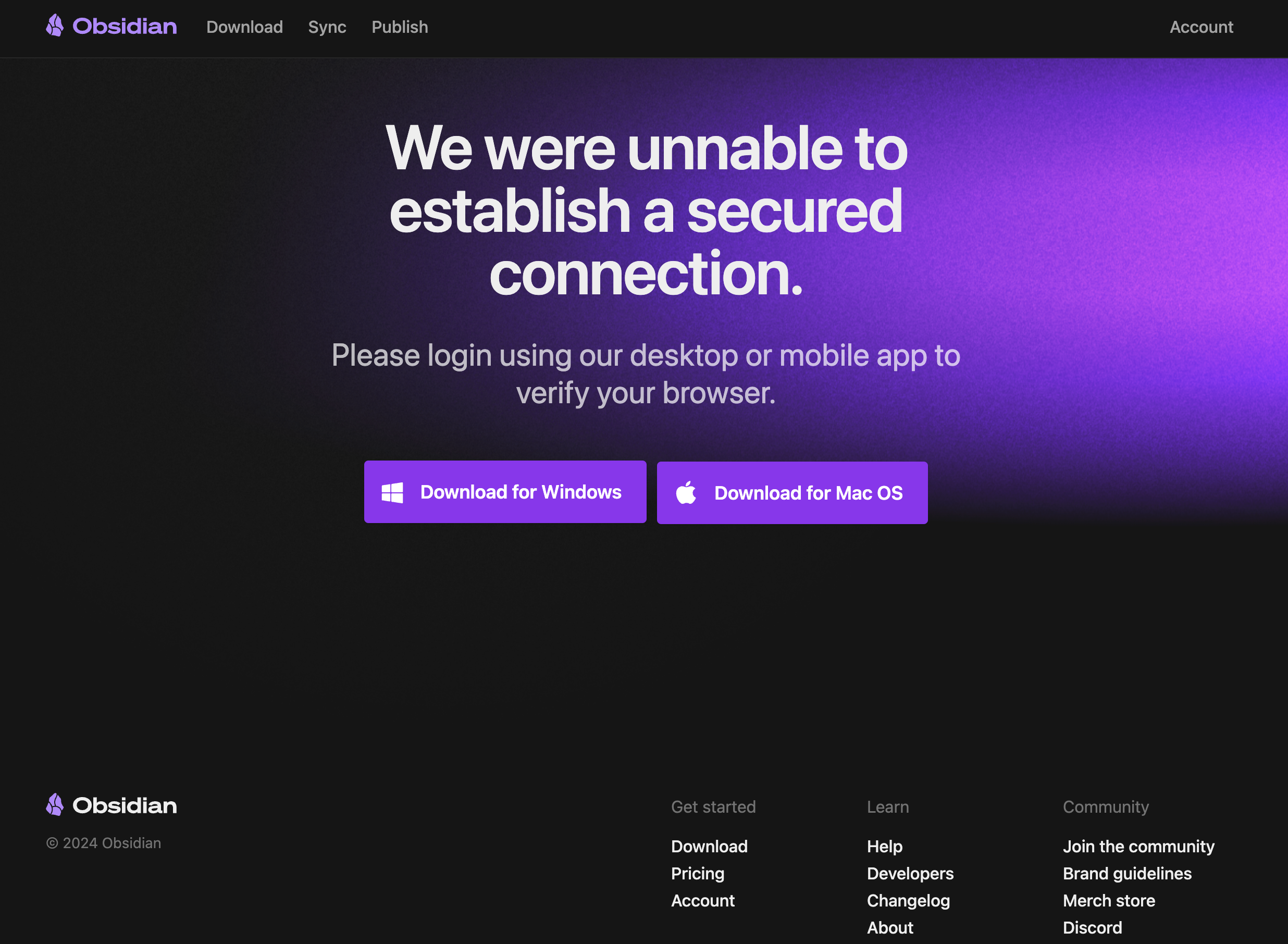
Phishing Website Analysis
The website is crafted well, closely mimicking the original website, and can easily lure users into clicking the “Download” button.
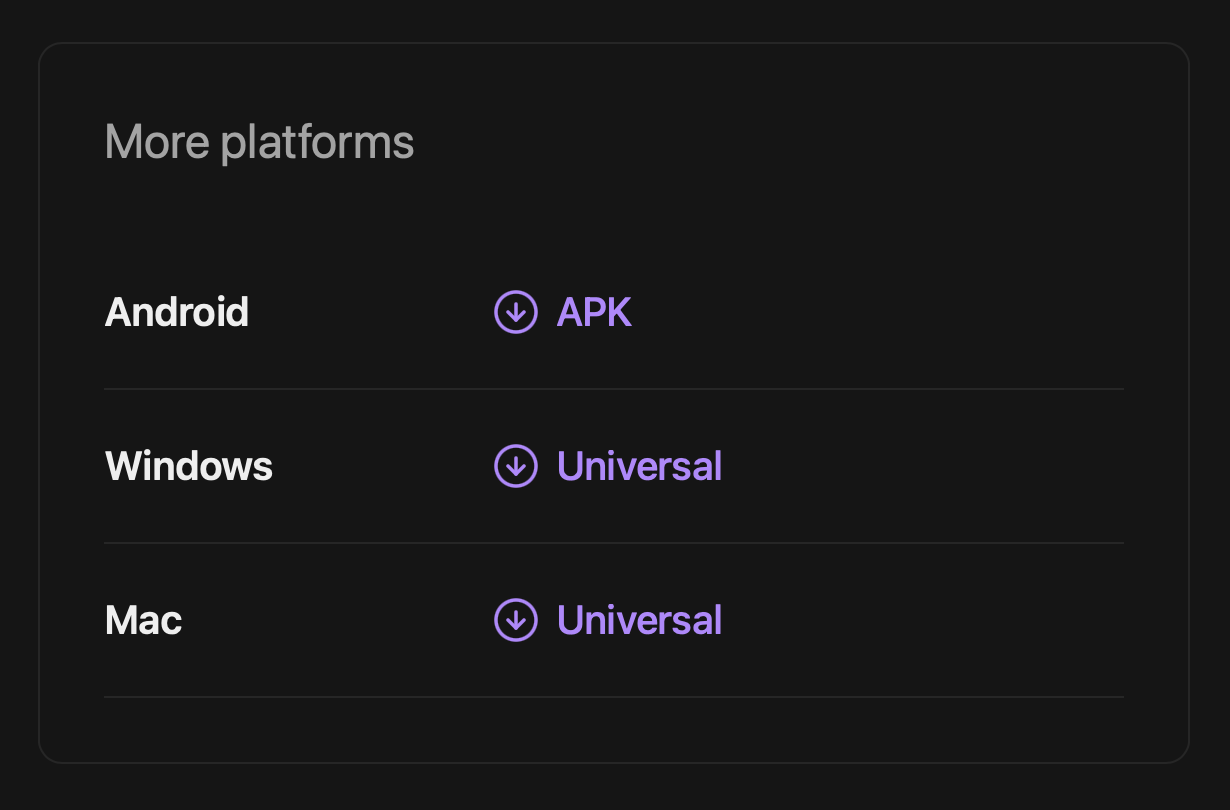
The website contains three download links for Android APK, macOS DMG, and Windows EXE payloads.
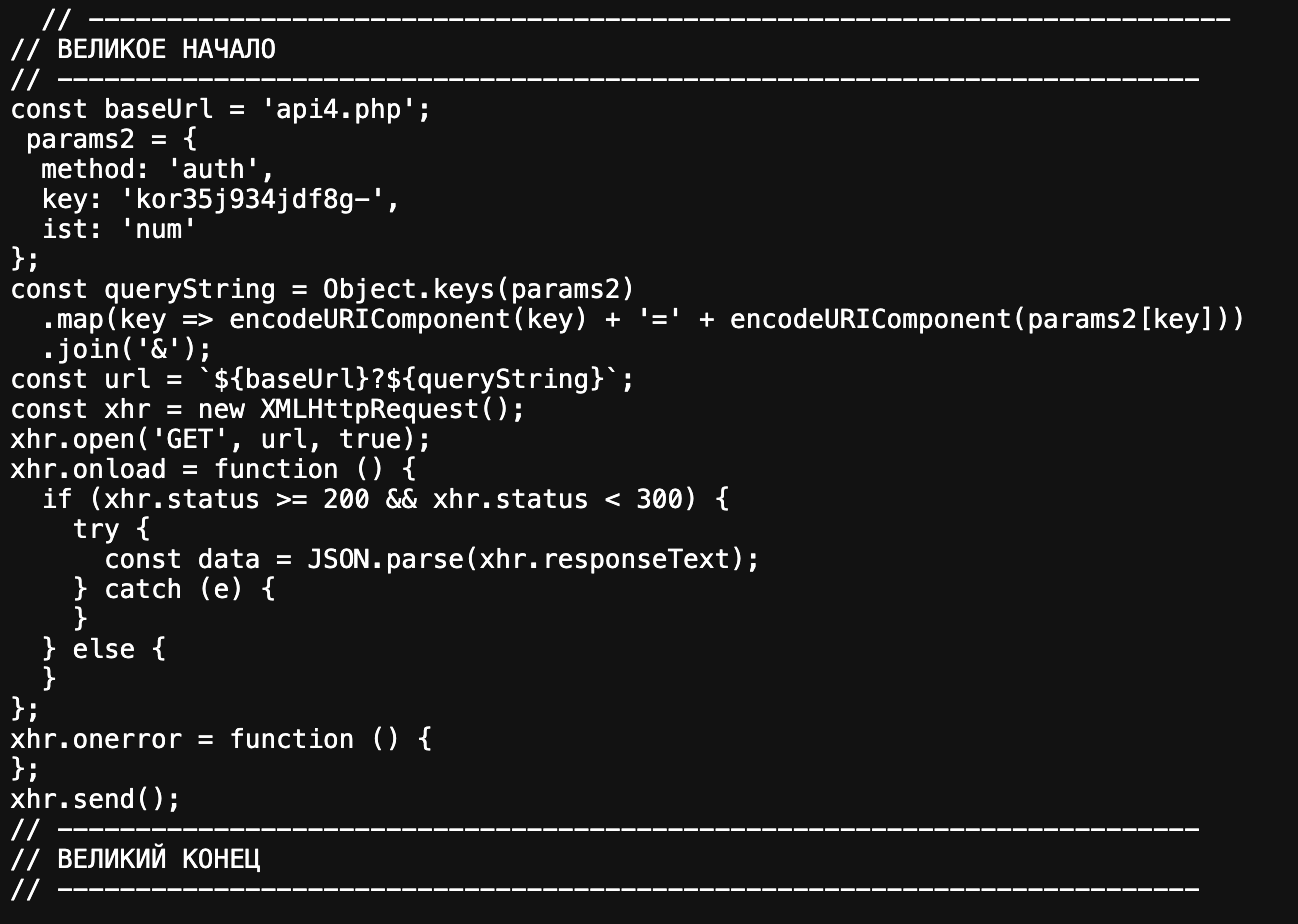
The website source contains a few comments written in Russian, including “Great Beginning” and “Great Ending,” among other less noticeable debugging comments:
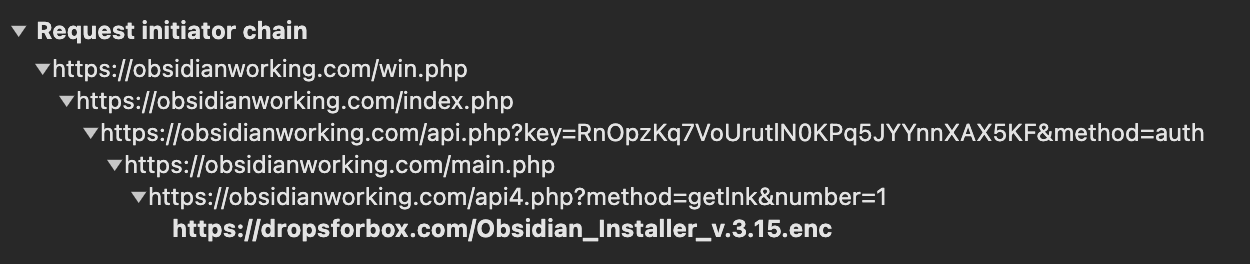
This is the request chain to download the Windows payload, which eventually leads to the recently registered domain dropsforbox[.]com, hidden behind CloudFlare like other noticeable phishing sites.
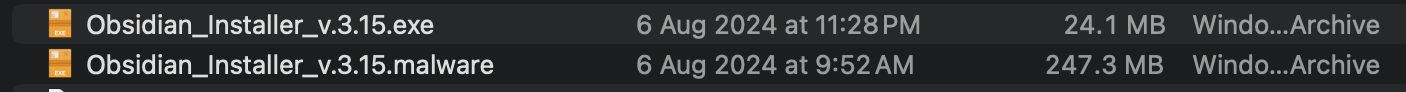
Another interesting observation is that the Windows payload has changed significantly in size compared to the previous version. Interestingly, the actual legitimate Obsidian installer weighs around 250 MB.
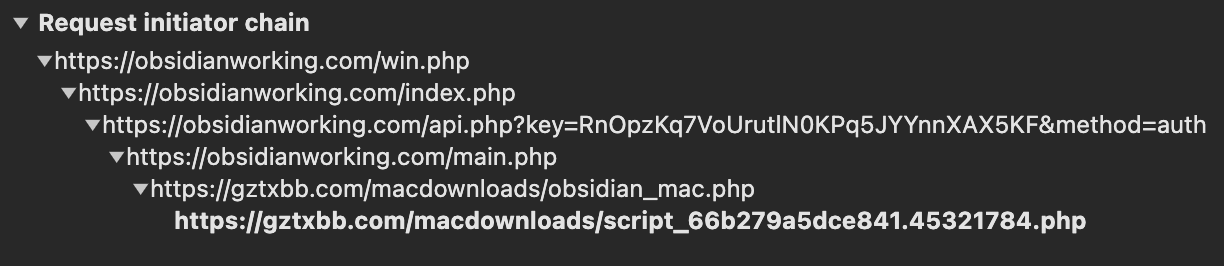
The request chain for downloading the macOS payload is even more interesting. It is dynamically generated, always producing different file sizes, names, and hashes. The payload is downloaded from another recently registered domain, gztxbb[.]com, which resolves to a Hetzner-owned IP 46[.]4.13.241. The phishing website and its code are updated in real time; the time between the screenshots below is less than 8 hours.
Before changes:
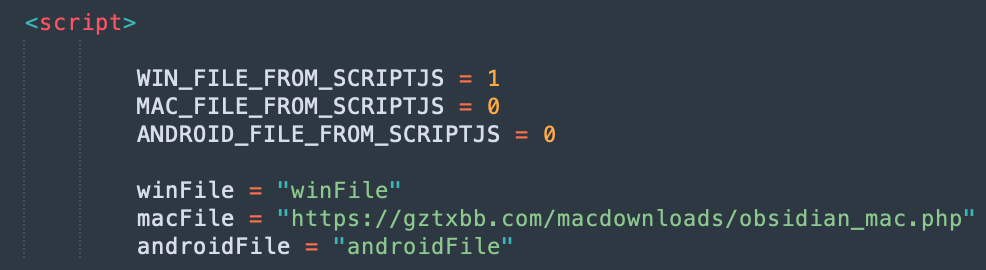
After changes:
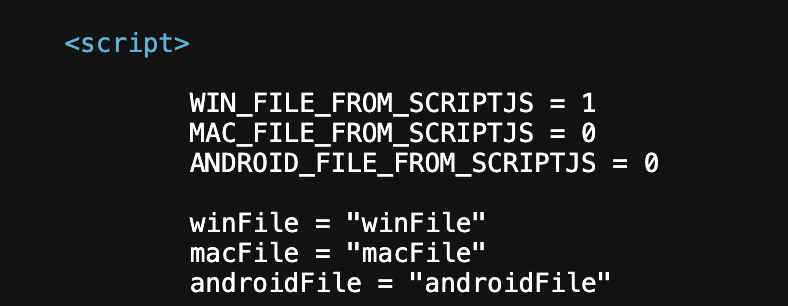
Requests Chain for macOS Payload:
After a while, Google Chrome started blocking download attempts:
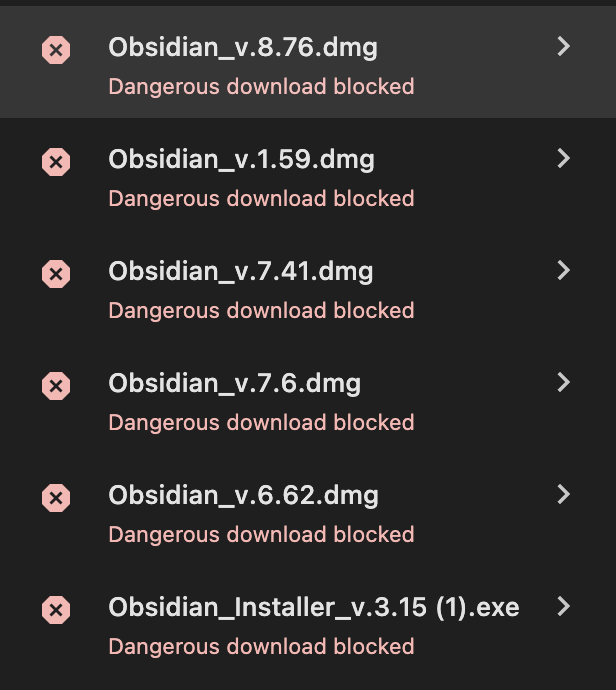
As seen, the macOS payload is dynamically generated on each download attempt.
Some other interesting script called by the website is located at https://adminforbusiness[.]com/statistic/js/stat.js and contains the JavaScript function displayed below:
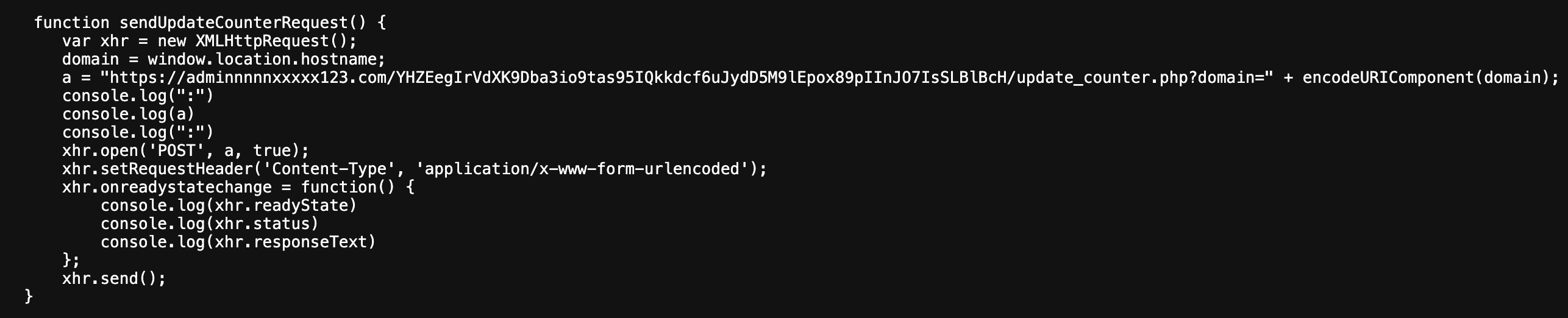
Based on its name and code, this function likely calls another PHP script on the domain adminnnnnxxxxx123[.]com, designated to count visits across multiple phishing domains.
The malware is allegedly an infostealer, following patterns observed in similar campaigns: SEO Poisoning, Google Ads abuse, and impersonation of popular tools.
IOCs
List of IOCs below—consider them for retro-hunting as malware infrastructure frequently changes:
obsidianworking.com– CloudFlare – Inactivegztxbb.com–46.4.13.241– Activedropsforbox.com– CloudFlare – Activeadminnnnnxxxxx123.com– CloudFlare – Activeadminforbusiness.com– CloudFlare – Active
obsidianworking.com
gztxbb.com
dropsforbox.com
adminnnnnxxxxx123.com
adminforbusiness.com
46.4.13.241
Hashes don’t make much sense, so I’ve uploaded some samples to VirusTotal and MalwareBazaar for further research. It’s odd that Windows samples have relatively low detection rates on VirusTotal:
- Obsidian_Installer_v.3.15.exe (larger size) – VirusTotal
- Obsidian_Installer_v.3.15.exe (smaller size) – VirusTotal, MalwareBazaar
Allegedly, the Windows infostealer is Rhadamanthys and the macOS infostealer is Atomic macOS Stealer.
Conclusion
Infostealers have long been a significant threat, but only recently have large companies recognized their impact. Attackers can bypass security by using stolen credentials. Organizations must focus on educating employees about safe online practices, such as using password managers instead of storing credentials in browsers.